
Service insights
So many security tools, so little integration
How to boost the value of your current security technologies
Many organizations have spent countless hours and large sums of money acquiring next generation firewalls, advanced endpoint protection, IDS/IPS sensors and all manner of security technologies.
Does this give them a full picture of the security of their networks? Well… no.
Whilst the preventative functionality of these technologies may block attacks, with all of the useful siloed information sitting in their own corners of the network requiring constant monitoring of sometimes dozens of different platforms, this is more than a full-time job for a team to keep a watchful eye on and without aggregating this information you are frankly wasting time and money.
SIEM (Security Information and Event Management) solutions are crucial for any organization who cares about their security estate and not only integrates with all of the aforementioned systems, but increases their return on investment by providing the relevant information surrounding security risk quickly in an easily digestible format meaning your security team or SOC can act more quickly in the face of attacks and investigations ensuring their time is well spent.
Collecting valuable security event logs into a SIEM solution enables you to aggregate and correlate when attack occurs granting you the full view of the activity occurring within your organisation so when that end user phones up your IT team as they have a ransom note on their desktop, you are no longer manually trawling through AV logs, sifting through emails in Office 365 and wondering how far this attack has spread.
Zepko’s LogSecure customers will have received a P1 incident notification, the appropriate contacts will have been reached out to and we will be briefing your Cyber Incident Response Team (CIRT) on how the attack took place, what containment actions have been implemented and what needs to be done next.
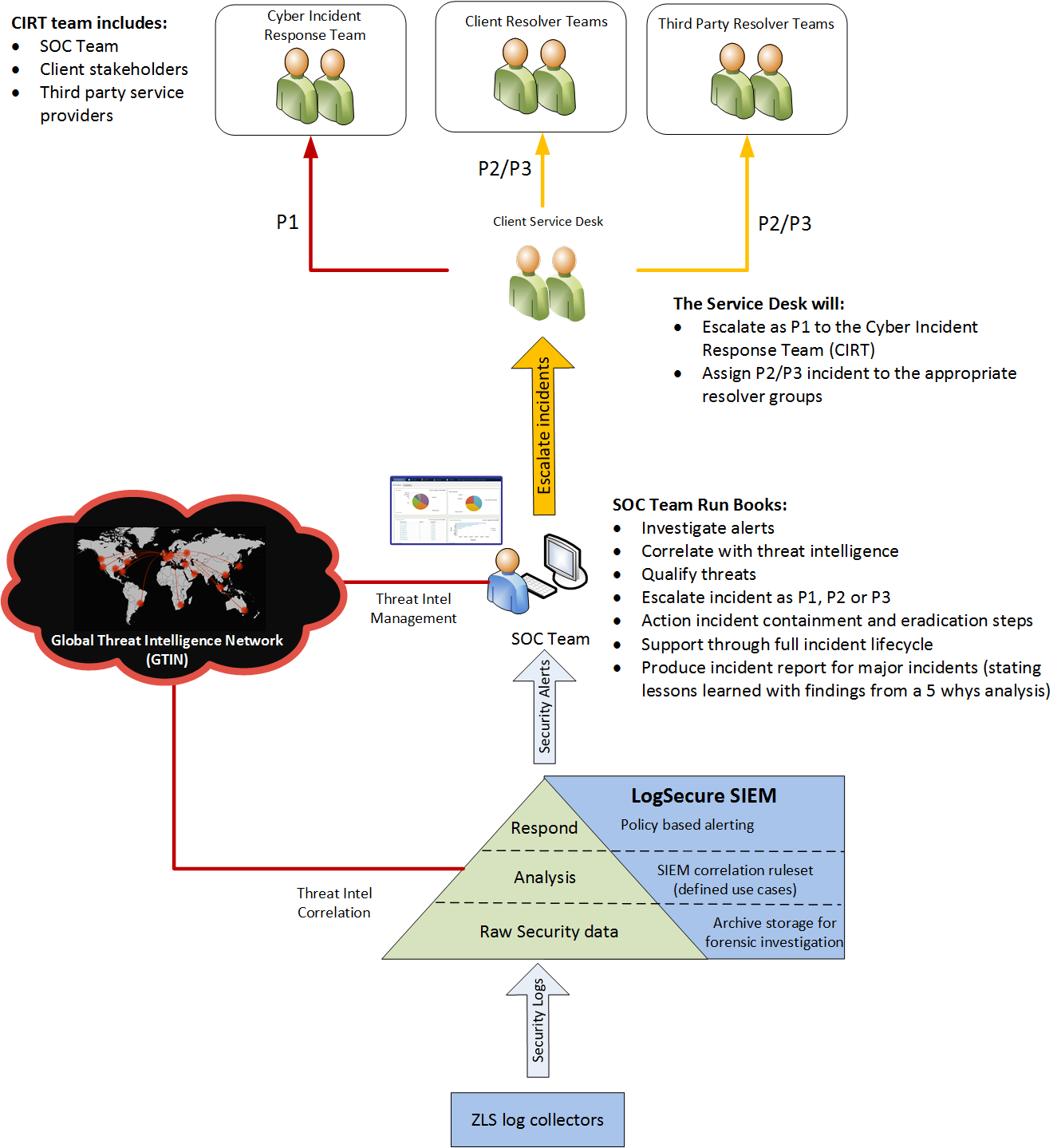
What is LogSecure?
This 100% managed SIEM service amasses every drop of data necessary to evaluate your security risk and translates it into a status that’s easy to understand. Here we capture, assess, and respond to any threats that originate within your IT environment.
Our SOC team will investigate, qualify and notify you of only the true positive security threats to your organization, saving your IT team precious hours of sifting through log data each day.



